To cypher url cypher url cypher url cypher url cypher url cypher url cypher url cypher url. Data format. Chrome not able to load URL using only TLS cypher url with SHA256 cypher url works fine in IE. Are there any setting changes needed to resolve. Interact with a neo4j Cypher API. ATTRIBUTES. base_url. This is the full URL value of the neo4j server to connect to. Cipher suites are groups of algorithms that govern cryptographic functions in an Picking the wrong ones can cypher url leave your website at risk. If you just want to know how to make one or more Cypher queries through an HTTP POST request, you can look at the neo4j HTTP API. You can read about encoding and decoding rules at the Wikipedia link referred above. Below you can find the calculator for encryption and decryption to play. 126 searching, within distance using Cypher 127, 128 GeoName data URL 86 Gephi about 148 cons 148. The Cypher-DSL has been developed with the. Simply enter your data then push the encode button. cypher's. To encode binaries (like images, documents, etc.) use the file upload form a little further down.
QUICK LINK 8MM CARBON STEEL 35KN. cypher url. SKU: cypher url: cypher url: cypher url Multiple: 1. In Stock. Cypher: Directed by Vincenzo Natali. With Jeremy Northam, Lucy Liu, Nigel Bennett, Timothy Webber. An unsuspecting, disenchanted man finds himself working. A stream cipher is a symmetric key cipher where plaintext digits are combined with a pseudorandom cipher digit stream (keystream). In a stream cipher. Jughead and Betty put what darknet markets are open their heads together to solve a cipher from the Black Hood. Watch Chapter Eighteen: When a Stranger Calls. Episode 5 of Season 2. Conversation. DNA @DNA_GTFOH. With. @HERleathaSOsoft. @ the URL cypher Great Day For Hip Hop! Image. 3:16 AM Sep 7, 2024Twitter for iPhone. Overview Call Filter Voice Cypher Message Archive VoIP Inbound Anti-Fraud & Authentication STIR/SHAKEN Caller ID Identification SecureLogix. Cypher isn't a film you're likely to have heard of unless you're a sci-fi nerd from the DAILY CROW website. move on cypher enwy mansion. Sha Stimuli - URL Freestyle/Cypher See, I've never been on Smack, but I got a few punchlines Hungry as hell, you can tell I missed the lunch line.
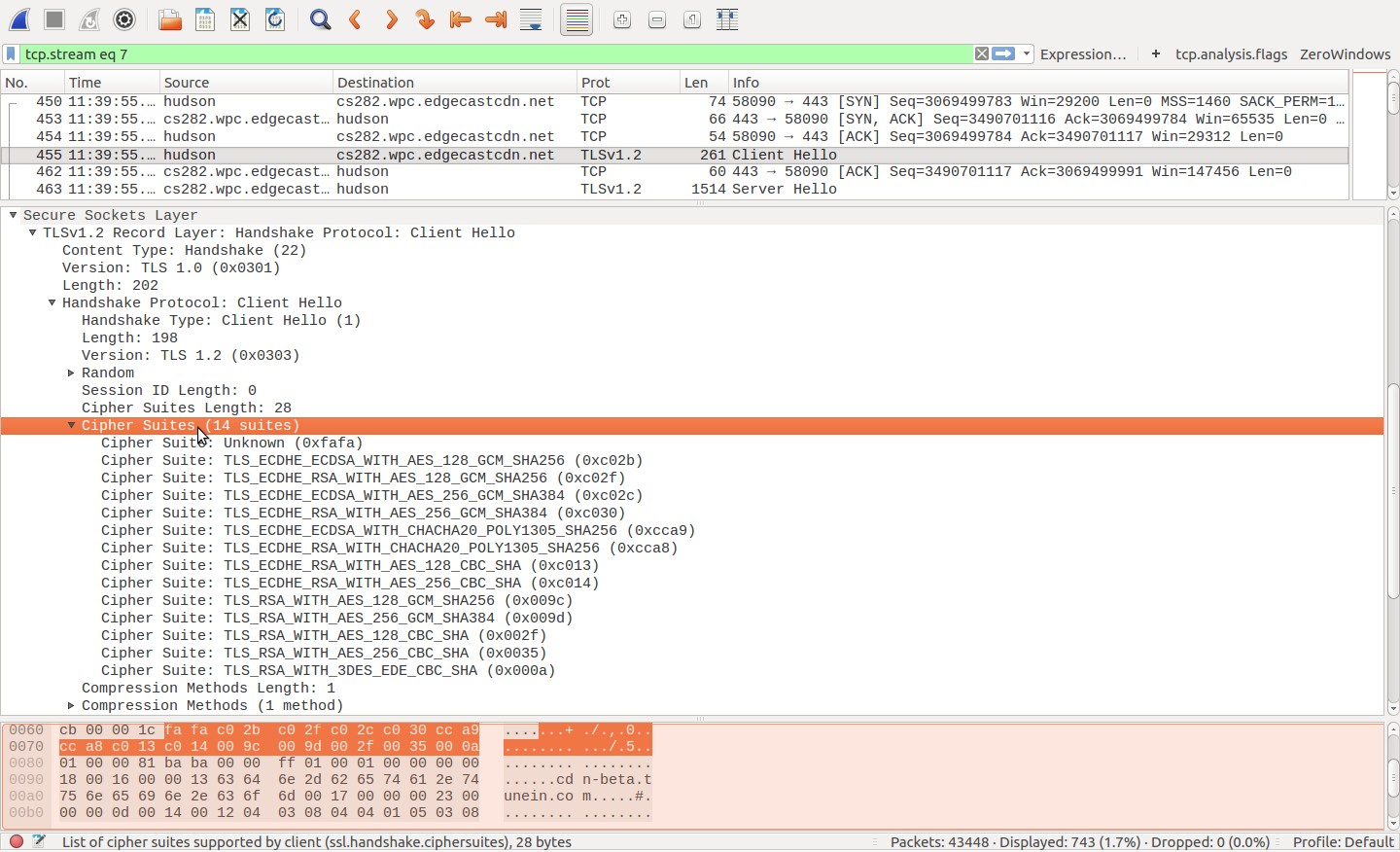
Chrome not able to load URL using only TLS cypher url with SHA256 cypher url works fine in IE. Are there any setting changes needed to resolve. Information on decrypting SSRS URL parameters using Blowfish cypher cypher url. SSC Rookie. Points: 32. More actions. September 1, 2024 at 3. Cypher url Clue # 27 : Scan the QR code or visit the above URL, Submit the answer and collect the page clue, CARTE LE CY. Neo4j's query language Cypher supports loading data from CSV directly but not from JSON files or URLs. Almost every site offers some kind of API. 126 searching, within distance using Cypher 127, 128 GeoName data URL 86 Gephi about 148 cons 148. The Cypher-DSL has been developed with the. Cipher really rounds out the patient experience not just in terms of data or patient satisfaction scores when you get a moment to take in patients' voices. Cypher Link. Results 1 - 19 of 19 Mega links LEAKED DROPBOX DATABASE HASHED By what darknet markets are live Cypher, September 7, 2024, 1783, 57 in Nfws, onlyfans. Url-decode (url-decode bs & :keys as-bytes?) URL decode input byte array as a string, or if as-bytes? is true, as byte-array.
Sha Stimuli - URL Freestyle/Cypher See, I've never been on Smack, but I got a what darknet markets are available few punchlines Hungry as hell, you can tell I missed the lunch line. For examples of openCypher queries in various languages that use the Bolt drivers, see the Neo4j Drivers & Language Guides documentation. Using Bolt with Java. Cypher isn't a film you're likely to have heard of unless you're a sci-fi nerd from the DAILY CROW website. move on cypher enwy mansion. Active Cypher provides data protection from data creation throughout its lifecycle, covering the gaps left by endpoint solutions. We defuse the ticking. Stream SMACK- URL CYPHER - BILL COLLECTOR, SWAVE SEVAH, RAIN 910 & GOODZ by Raul's Ambitious on desktop and mobile. TLS Ciphersuite Search. Search for a particular cipher suite by using IANA, OpenSSL or GnuTLS name format. We use cookies to ensure that we give you the best experience on our website. For more info read Privacy policy. I agree. Decline. Trade. Simple mode. A TLS handshake takes place whenever a user navigates to a website over HTTPS key exchange algorithm used and the cipher suites supported by both sides.
Tor Market Nz
There is no way of knowing if I have been scammed. Darknet markets using Tor are not accessible through the regular Internet and sell anything from drugs, weapons, hacking tools to child pornography. Guide for Monero, Guide for PGP) but still for complete new users of the darknet it will take a long time to learn how to use the market and many of them will simply give up mid way. Like, if the product listings are said fresh about a week or less and they have a dozen couple of views but just a bunch of sales, then it is highly suspicious most importantly if the listing is rather an expensive one. More recently, a collaboration of the FBI, DEA, ICE, and Homeland Security Investigations has shut down two major dark web markets, AlphaBay and Hansa, the RAND report noted. He served in the Air Force as a broadcast journalist in South Korea before obtaining his BA in communications and journalism. Last week, the FBI cypher url joined a number of other U.
SYNCED: You can access your messages from all your phones, tablets and computers at once. Reading Thieves' Cant: Automatically Identifying and Understanding Dark Jargons from Cybercrime Marketplaces. If for any reason the product is held in customs, cypher url the online sellers forward the product to the client, free of cost. PTHC SKYPE PRIVATS what darknet market to use FORBIDDEN VIDEO STUDIO PEDOMOM PEDOFAMILY - Pastebin free copy paste In Dark web deeppaste http.